Isgabrillo's hit the nail on the head for accessing the Cisco VPN Client. If you want an alternative, you can also look at the Shrew Soft VPN Client (free download) at shrew.net or The Greenbow at thegreenbow.com. Hello Cisco community members, I am trying to configure cisco easy vpn remote (client) on cisco router C1101-4p (Cisco IOS XE Software, Version 16.09.02 Cisco IOS Software Fuji, ISR Software (ARMV8EBLINUXIOSD-UNIVERSALK9IAS-M), Version 16.9.2.
Home > Cisco Systems, Inc.
File extension list filtered by software name
Cisco VPN Client
Found one file extension association related to Cisco VPN Client and 1 file format developed specifically for use with Cisco VPN Client.
Platform, operating system:Microsoft Windows

Go to: Cisco VPN Client description
Developer:Cisco Systems, Inc.
Cisco software list & details
Bookmark & share this page with others:
Cisco VPN Client
Developer / company:Cisco
Simple to deploy and operate, the Cisco VPN Client allows organizations to establish end-to-end, encrypted VPN tunnels for secure connectivity for mobile employees or teleworkers. This thin design, IP security (IPSec) implementation is compatible with all Cisco virtual private network (VPN) products.
The Cisco VPN Client can be pre-configured for mass deployments, and initial logins require little user intervention. It supports the innovative Cisco Easy VPN capabilities, delivering a uniquely scalable, cost-effective, and easy-to-manage remote access VPN architecture that eliminates the operational costs associated with maintaining a consistent policy and key management method. The Cisco Easy VPN feature allows the Cisco VPN Client to receive security policies upon a VPN tunnel connection from the central site VPN device (Cisco Easy VPN Server), minimizing configuration requirements at the remote location. This simple and highly scalable solution is ideal for large remote access deployments where it is impractical to individually configure policies for multiple remote PCs.
Cisco VPN Client icon
Cisco VPN Client icon
size: 128px x 128px (.png with transparency)
Cisco VPN Client works with the following file extensions:
Note: You can click on any file extension link from the list below, to view its detailed information. The list of extensions used or otherwise associated with the application may not be complete, because many common file extensions on our website, such as jpg (pictures) or txt (text files), can be opened by a large number of applications, or are too general file format. However most, if not all directly associated file extensions should be listed with its appropriate program. Although its likely, that some file extensions may be missing from the list of associated file extensions with the application, yet they can be opened, be part of, or otherwise be associated with the program.
Cisco VPN Client default file extension associations
.pcf
Comparison table of actions that Cisco VPN Client can perform with its associated file type beta
This table might not contain all possible associated or supported file types or may contain incorrect data.
If you need more information please contact the developers of Cisco VPN Client (Cisco Systems, Inc.), or check out their product website.
File type Action | Open | Save | Edit | View | Play | Convert | Create | Record | Import | Export | Burn | Extract | Recover | Backup | Settings | Other | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Yes | Yes | Yes | - | - | - | Yes | - | - | - | - | - | - | - | - | Yes | - |
For more information on Security, visit our Security Reference Guide or sign up for our Security Newsletter
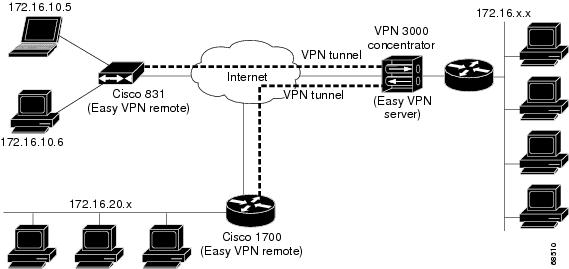
Telecommuting is increasingly becoming a part of everyday life, and IPSec connectivity is arguably the most popular connection method that telecommuters use to connect to a VPN across the public Internet. Given that telecommuters can be anywhere in the Internet, the successful completion of authorization and authentication is critical for granting access to the VPN. This chapter explores authentication and authorization models for the IPSec telecommuter.
Cisco Easy Connect Vpn
Extended Authentication (XAUTH) and Mode Configuration (MODE-CFG)
Authentication schemes such as Remote Authentication Dial-In User Service (RADIUS) and SecureID are commonly used for providing secure remote access. It is highly desirable to leverage these authentication mechanisms for IPSec remote access. But Internet Key Exchange (IKE) protocol, which you learned about in Chapter 2, 'IPSec Overview,' does not provide a method to leverage these unidirectional authentication schemes. Extended Authentication, commonly referred to as XAUTH, was developed to leverage these legacy authentication schemes with IKE.
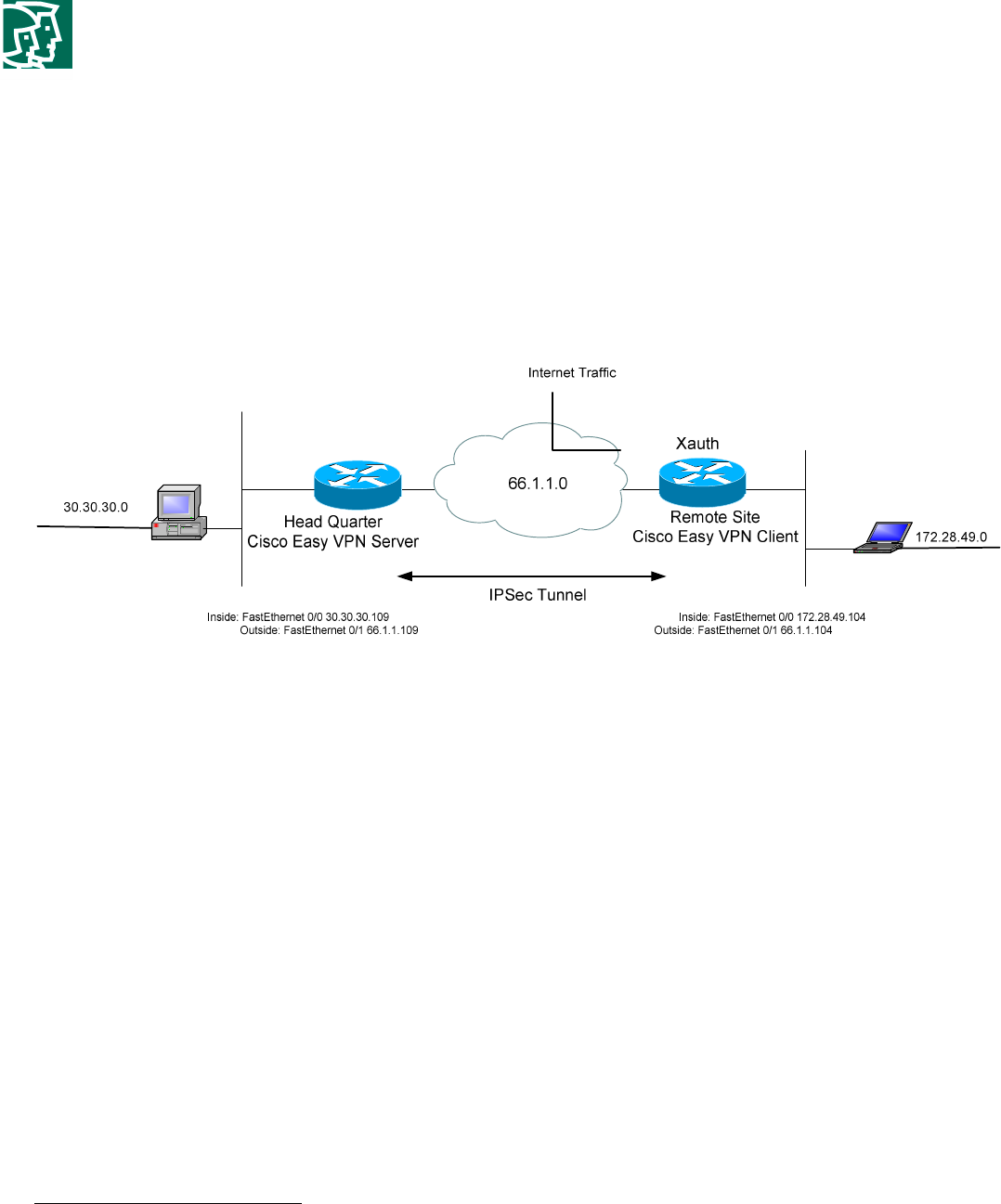
XAUTH provides an additional level of authentication by allowing the IPSec gateway to request extended authentication from remote users, thus forcing remote users to respond with their credentials before being allowed access to the VPN. It should be noted that XAUTH functions by first forming an IKE phase 1 SA using conventional IKE, and then by extending the IKE exchange to include additional user authentication exchanges. Figure 4-1 shows an XAUTH exchange using a generic username and password authentication scheme.
Figure 4-1 Extended Authentication (XAUTH) Exchange
As shown in Figure 4-1, XAUTH uses a Request/Reply mechanism to provide the extended authentication. The XAUTH process is terminated, either when the gateway starts a SET/ACK exchange, which includes an XAUTH_STATUS attribute, or when the remote device sends a XAUTH_STATUS attribute in a REPLY message.
The XAUTH protocol defines four message types that are exchanged between the remote user and the IPSec gateway. These messages carry various attributes for the extended authentication process to work. The four XAUTH message types are:
- ISAKMP_CFG_REQUEST
- ISAKMP_CFG_REPLY
- ISAKMP_CFG_SET
- ISAKMP_CFG_ACK
A description of the XAUTH message types follows:
- ISAKMP_CFG_REQUEST— This message is sent from the IPSec gateway to the IPSec client requesting extended authentication of the client.
- ISAKMP_CFG_REPLY— This message must contain the filled-in authentication attributes that were requested by the gateway or, if the proper authentication attributes cannot be retrieved, this message must contain the XAUTH_STATUS attribute with a value of FAIL.
- ISAKMP_CFG_SET— This message is sent from the gateway and is used only to state the success or failure of the authentication.
- ISAKMP_CFG_ACK— This message is sent from the IPSec client, acknowledging receipt of the authentication result.
The XAUTH message types defined above carry various attributes. A brief description of the attributes is shown in Table 4-1.
Table 4-1. XAUTH Attributes
Attribute | Description |
XAUTH_TYPE | This attribute describes the type of extended authentication method requested. Four authentication methods are defined in the protocol: Generic, RADIUS_CHAP, One Time password (OTP), and Secure ID. This is an optional attribute for the ISAKMP_CFG_REQUEST and ISAKMP_CFG_REPLY messages. The XAUTH_TYPE in a REPLY must be identical to the XAUTH_TYPE in the REQUEST. However, an XAUTH transaction may have multiple REQUEST/REPLY pairs with different XAUTH_TYPE values in each pair. |
XAUTH_USER_NAME | The username may be any unique identifier of the user, such as a login name, an email address, or a X.500 Distinguished Name. |
Apple keypad & mouse. XAUTH_USER_PASSWORD | The user's password. |
XAUTH_PASSCODE | A token card's passcode. |
XAUTH_MESSAGE | A textual message from the gateway to the IPSec client. The message may contain a textual challenge or instruction. |
XAUTH_CHALLENGE | A challenge string sent from the gateway to the IPSec client to be included in its calculation of a password. Where can i download mac os high sierra. This attribute should be sent only in an ISAKMP_CFG_REQUEST message. Typically, the XAUTH_TYPE attribute dictates how the receiving device should handle the challenge. For example, RADIUS-CHAP uses the challenge to hide the password. |
XAUTH_STATUS Double click on the installation file PDFStudiomac64.dmg to mount the disk image, then double click on the mounted image. Finally double click on the installer PDF Studio Installer. PDF Studio works on macOS 11.0 (Big Sur), macOS 10.15 (Catalina), macOS 10.14 (Mojave), macOS 10.13 (High Sierra), macOS 10.12 (Sierra), Mac OS X 10.11 (El. PDF Studio Standard. Coupon (Optional): (applied next screen) Qty US $ 89.00 for 1 copy. Pdf studio standard. PDF Studio™ is an all-in-one, easy to use PDF editor that provides all PDF features needed (see features comparison with Acrobat) at one third the price of Adobe® Acrobat® and maintains full compatibility with the Adobe PDF Standards. 1/3 the price of Adobe Acrobat. Deploy to more users for same price. Works on Windows, Mac, & Linux. | A variable that is used to denote authentication success (OK=1) or failure (FAIL=0). This attribute must be sent in the ISAKMP_CFG_SET message, in which case it may be set to either OK or FAIL, and may be sent in a REPLY message by a remote peer, in which case it must be set to FAIL. |
When a remote access user connects to an IPSec gateway and XAUTH is required by the gateway, configuration on the gateway initiates the XAUTH messages before IKE phase 2 negotiation begins. If the remote access client does not have support for the authentication method requested by the gateway, the client would send back a REPLY with the XAUTH_STATUS attribute set to FAIL, thus failing the authentication.
Cisco Easy Vpn Client Software
Example 4-1 shows the configuration of XAUTH using the RADIUS/AAA authentication method.
Example 4-1. Cisco IOS XAUTH Configuration on the IPSec Gateway
The addition of the following command on the crypto map enables XAUTH and triggers the XAUTH transaction after IKE phase 1 and before IKE phase 2:
Cisco Easy Vpn Client Download
As you learned in Chapter 2, 'IPSec Overview,' a very common deployment scenario for IPSec telecommuters is the use of IKE pre-shared key authentication with Aggressive Mode. The primary motivation for this scenario is that the IP address of an IPSec remote access user connecting to an IPSec gateway over the public Internet is typically not known in advance to the gateway. In most deployments using pre-shared keys, a single shared group key is used for all users of the VPN. What this means is that without employing some form of additional user authentication, there is no way to verify that the person connecting with that VPN client is indeed a valid user.
Imagine, for example, a situation where a laptop with a VPN client is stolen—because the VPN client is already configured with a valid group key, anyone with the laptop can connect to the VPN without any problems, as no further authentication is required! Extended Authentication (XAUTH) is widely employed to address this serious security gap. XAUTH forces users to identify themselves with a user id and a password after the group pre-shared key has been verified.
XAUTH is also referred to as 'two factor authentication.' The password could be a 'one-time password' (for example, from a SecureID card) adding further security to such a deployment. Although the usage of XAUTH is very common and desired for the telecommuter scenario using pre-shared keys and Aggressive Mode, it can also be used with Main Mode and other authentication methods such as digital certificates. It is important to note that although XAUTH is deployed very commonly, it has not been established as a standard by the IPSec working group in the IETF, which means that it may present interoperability issues among different vendor implementations.
